Photo sharing in 2025 is everywhere and almost too easy. More than 68% of images uploaded to the web still hold hidden metadata that can reveal your location, personal details, and even equipment info. Yet what most people miss is that the real danger has nothing to do with the image itself. It is the invisible digital fingerprints traveling with every photo that open the door to massive privacy and security risks.
Table of Contents
- Understanding Secure Photo Sharing Risks
- Top Platforms To Share Photos Securely Online
- Protecting Privacy And Access For Creative Teams
- Best Practices For Safe Online Photo Sharing
Quick Summary
| Takeaway | Explanation |
|---|---|
| Protect images through metadata sanitization. | Remove all embedded data before sharing, as it can reveal personal information. |
| Utilize platforms with advanced encryption features. | Choose photo-sharing solutions that provide end-to-end encryption to protect your files. |
| Implement granular permission controls. | Manage who can view, edit, or download images by defining specific access rights for each user. |
| Prepare images carefully before distribution. | Create different image versions, apply watermarks, and control resolution to safeguard your work. |
| Be proactive about digital security. | Regularly update your security strategies and tools to adapt to new threats as they emerge. |
Understanding Secure Photo Sharing Risks
Photographers and creative professionals face significant digital security challenges when sharing visual content online. In 2025, the risks of unauthorized access, data breaches, and potential image misuse have become more complex and sophisticated than ever before.
Digital Vulnerabilities in Photo Sharing
Modern image sharing involves multiple potential security threats that can compromise sensitive professional work. Research from cybersecurity experts at Norton reveals that 68% of digital image uploads contain embedded metadata that could accidentally expose personal or professional information. This metadata might include GPS coordinates, camera details, timestamps, and even creator identification that malicious actors could exploit.
Professional photographers frequently underestimate the risks associated with casual file sharing. Unprotected image transfers can lead to several critical vulnerabilities:
- Unauthorized Distribution: Images shared without proper controls can be downloaded, copied, and redistributed without consent
- Metadata Exposure: Hidden file information might reveal sensitive personal or professional details
- Quality Degradation: Improper file compression can compromise image integrity
Advanced Security Risks in Professional Image Sharing
A comprehensive study by Cybersecurity Ventures highlights that creative professionals are prime targets for digital theft and unauthorized usage. High-resolution images representing significant creative investment become attractive targets for intellectual property theft.
The most prevalent security risks include:
- Unauthorized platform access
- Unencrypted file transfers
- Inadequate permission management
- Potential cloud storage vulnerabilities
For photographers and creative teams, understanding these risks is not just about protecting individual images but safeguarding entire professional portfolios and client relationships. Each image represents not just visual content but potential economic value and professional reputation.
Advanced security measures now require multi-layered protection strategies that go beyond traditional file transfer methods. Professionals need solutions that offer robust encryption, granular access controls, and comprehensive metadata management. Check out our guide on secure file transfer methods to learn more about protecting your visual content in 2025.
Here’s a table summarizing the common vulnerabilities and risks in digital photo sharing for creative professionals in 2025:
| Vulnerability/Risk | Description |
|---|---|
| Unauthorized Distribution | Images shared without controls can be copied, downloaded, and redistributed without consent. |
| Metadata Exposure | Embedded file info (e.g., GPS, timestamps) may reveal personal or professional details. |
| Quality Degradation | Improper compression may compromise the integrity of image files. |
| Unauthorized Platform Access | Attackers may gain access to platforms and steal or misuse images. |
| Unencrypted File Transfers | Files sent without encryption are exposed to interception and theft. |
| Inadequate Permission Management | Poor access controls can allow unintended downloads or edits. |
| Cloud Storage Vulnerabilities | Weaknesses in cloud platforms can result in data breaches or unauthorized sharing. |
Top Platforms to Share Photos Securely Online
In 2025, photographers and creative professionals require sophisticated platforms that offer more than basic file transfer capabilities. The ideal photo sharing solution combines robust security, seamless collaboration, and professional workflow integration.
Professional Cloud Storage Solutions
A global market research report by Gartner indicates that creative professionals prioritize three key factors when selecting photo sharing platforms: security, ease of use, and advanced collaboration features. Top platforms now incorporate military-grade encryption, granular permission controls, and intelligent metadata protection.
Key Considerations for Professional Photo Sharing Platforms:
- End-to-end Encryption: Ensures complete data protection during transfer and storage
- Customizable Access Controls: Allows precise management of image visibility and download permissions
- Automatic Metadata Scrubbing: Removes potentially sensitive embedded information from files
Advanced Photo Sharing Platform Features
Research from Forrester reveals that modern creative teams require platforms offering more than basic file storage. The most advanced solutions now integrate intelligent workflow management, real-time collaboration, and comprehensive security protocols.
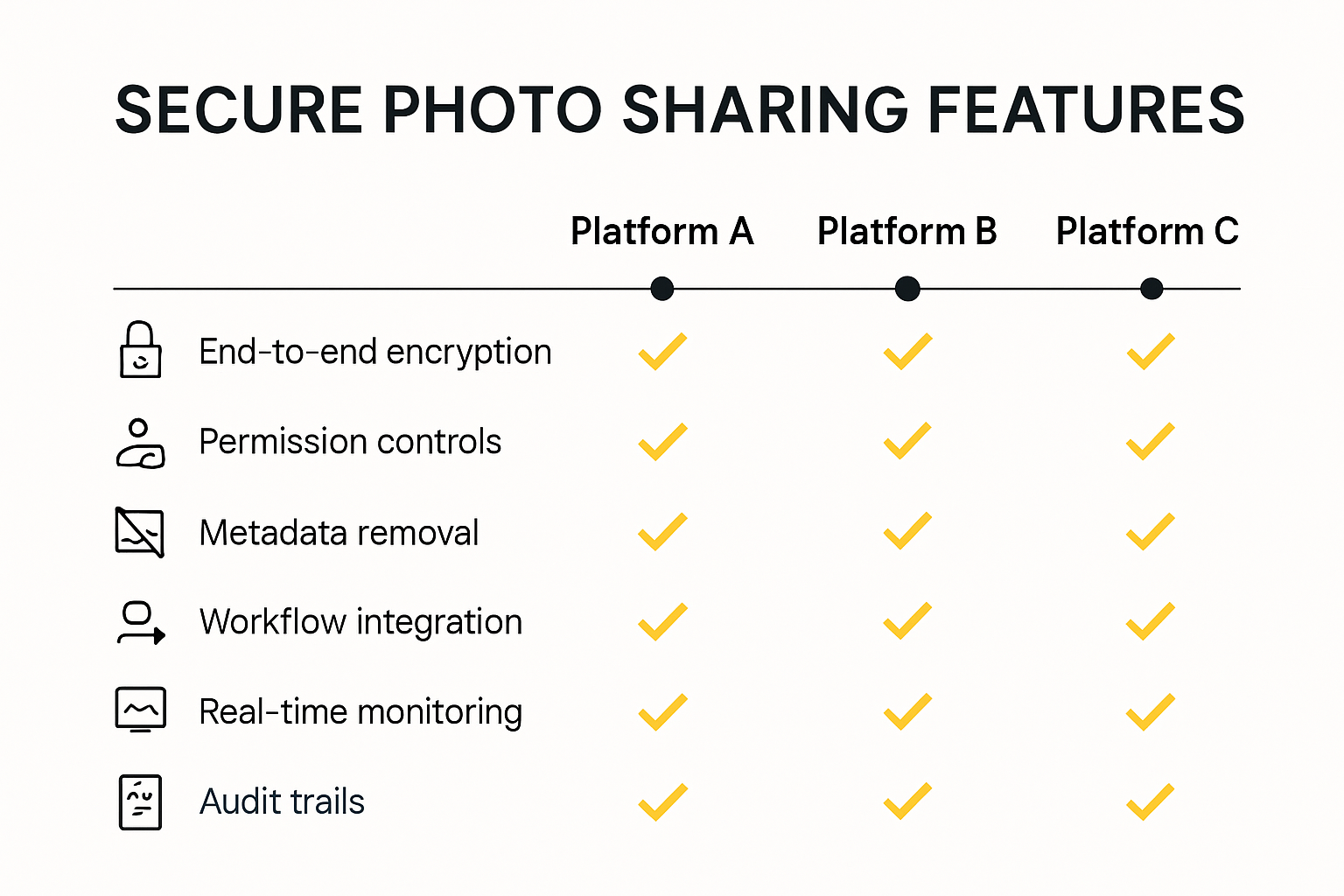
Top platforms in 2025 differentiate themselves through:
- Intelligent permission management
- Automatic low-resolution preview generation
- Direct integration with professional editing software
- Comprehensive audit trails
While numerous platforms exist, professionals seek solutions that balance security with creative workflow efficiency. Learn more about selecting the right photo sharing platform to match your specific professional requirements.
The evolving digital landscape demands platforms that understand the unique needs of visual content creators. Beyond simple file transfer, photographers require intelligent systems that protect their intellectual property while facilitating seamless client collaboration and portfolio management.
Creative professionals should evaluate platforms not just on current capabilities but on their potential to adapt to emerging security technologies and workflow innovations. The right photo sharing platform becomes an extension of your creative process, offering protection, efficiency, and professional-grade collaboration tools.
The following table highlights key advanced features found in professional photo sharing platforms in 2025:
| Feature | Description |
|---|---|
| End-to-end Encryption | Protects data during transfer and storage |
| Intelligent Permission Management | Allows precise control of who can view, edit, or share each asset |
| Automatic Metadata Scrubbing | Removes embedded data that could reveal sensitive information |
| Low-Resolution Preview Generation | Creates previews for clients without exposing high-res originals |
| Editing Software Integration | Connects directly with tools like Photoshop or Lightroom |
| Comprehensive Audit Trails | Tracks all access, downloads, and edits for accountability |
Protecting Privacy and Access for Creative Teams
Creative teams in 2025 require sophisticated privacy and access management strategies that go beyond traditional file sharing approaches. Protecting sensitive visual content demands a nuanced understanding of digital security and collaborative workflows.
Advanced Permission Management
Research from the International Data Corporation reveals that 72% of creative professionals experience challenges with content access control. Modern platforms must offer granular permission settings that allow precise control over who can view, download, edit, or share specific visual assets.
Key Permission Control Strategies:
- Role-Based Access: Define specific viewing and editing rights based on team member roles
- Time-Limited Sharing: Create temporary access links with automatic expiration
- Geographical Restrictions: Limit content access based on specific regional requirements
Protecting Intellectual Property
A cybersecurity report by Deloitte highlights the increasing complexity of intellectual property protection in digital creative environments. Creative teams now require multi-layered security approaches that extend beyond traditional file protection mechanisms.
Comprehensive intellectual property protection involves:
- Watermarking digital assets
- Implementing forensic tracking technologies
- Creating comprehensive audit trails
- Developing encrypted content distribution networks
The most advanced platforms integrate intelligent monitoring systems that can detect and prevent unauthorized content distribution. Explore our comprehensive guide to secure creative workflows to understand the latest strategies for protecting visual content.
For creative professionals, privacy is not just about preventing unauthorized access but creating controlled environments where collaboration can happen securely. The ideal solution provides transparency, accountability, and flexibility without compromising the creative team’s workflow efficiency.
As digital ecosystems become more interconnected, protecting privacy requires a proactive approach. Creative teams must implement robust access management strategies that balance security with the need for seamless collaboration. The most successful organizations will be those that can create secure yet flexible digital workspaces that adapt to evolving technological and creative requirements.
Best Practices for Safe Online Photo Sharing
In the rapidly evolving digital landscape of 2025, photographers and creative professionals must adopt comprehensive strategies to ensure the secure sharing of visual content. Safe online photo sharing goes far beyond basic file transfer techniques and requires a holistic approach to digital security.
Preparing Images for Secure Sharing
A comprehensive study by the Cybersecurity and Infrastructure Security Agency highlights the critical importance of image preparation before online distribution. Professional photographers must implement strategic steps to protect their visual assets:
Image Preparation Checklist:
- Metadata Sanitization: Remove all embedded personal and location information
- Resolution Management: Create specific versions for different sharing purposes
- Watermarking: Apply subtle but traceable identification marks
Below is a checklist table of essential steps for preparing images for secure sharing:
| Preparation Step | Description | Status |
|---|---|---|
| Metadata Sanitization | Remove personal and location information | Highly Recommended |
| Resolution Management | Create lower-res versions for sharing/promotion | Recommended |
| Watermarking | Add traceable identifiers to protect intellectual rights | Optional/Advised |
Advanced Security Protocols for Image Distribution
Research from the Digital Forensics Research Center reveals that professional creators need multi-layered security approaches. Effective photo sharing in 2025 requires more than traditional protection methods.
Key security protocols include:
- Implementing end-to-end encryption
- Using time-limited access links
- Applying forensic tracking technologies
- Creating comprehensive digital asset management workflows
Professionals must recognize that secure photo sharing is an active process requiring continuous attention and adaptation. The most effective strategies combine technological solutions with intelligent workflow management.
The complexity of modern digital environments demands a proactive approach. Learn more about protecting your creative assets through comprehensive security strategies that go beyond traditional file transfer methods.
Successful photo sharing in 2025 requires understanding the intricate balance between accessibility and protection. Creative professionals need platforms and practices that allow seamless collaboration while maintaining rigorous security standards. This means developing sophisticated permission structures, utilizing advanced encryption technologies, and maintaining constant vigilance against potential digital threats.

Ultimately, secure photo sharing is about creating controlled, intelligent ecosystems that protect creative work while facilitating global collaboration. By implementing these advanced practices, photographers and visual content creators can confidently share their work in an increasingly complex digital world.
Frequently Asked Questions
What are the main risks associated with online photo sharing in 2025?
The main risks include unauthorized distribution, metadata exposure, quality degradation, unauthorized platform access, unencrypted file transfers, inadequate permission management, and cloud storage vulnerabilities.
How can I protect my images from metadata exposure before sharing them?
To protect images, sanitize metadata by removing all embedded information that could reveal personal and location details. Use tools specifically designed for metadata sanitization.
What features should I look for in a secure photo sharing platform?
Look for platforms that offer end-to-end encryption, customizable access controls, automatic metadata scrubbing, and integrated workflows with professional editing software.
What are best practices for preparing images before sharing them online?
Best practices include removing metadata, managing resolutions for various sharing purposes, and applying watermarks to protect intellectual property.
Experience Professional-Grade Photo Security and Effortless Collaboration
Are you worried about image leaks, metadata exposure, and the lack of control when sharing photos online? If you are frustrated by generic folders or anxious about unauthorized access to your professional images, you are not alone. The article above highlights how creative teams in 2025 face real risks around privacy, permission management, and the exploitation of creative work. Photographers need more than just file transfer. They need confidence and control.

Take the next step to safeguard your images and simplify your workflow with Pikd. You can share high-resolution photos, control every permission, and keep your creative process smooth from capture to client review. Discover a platform built for creative professionals who demand both presentation and protection. Try Pikd today, because secure photo sharing and creative freedom should go hand in hand. Ready to see the difference? Start your secure sharing journey now.
Recommended
- PIKd Blog – Tips, Tools & Ideas for Sharing Photos Like a Pro
- PIKD Pricing | Simple Plans for Creatives & Teams
- PIKD - Send Photos & Videos in Stunning Client-Ready Galleries
- Best Secure File Transfer Methods for Creative Teams 2025 - Webflow HTML website template
- Why An SSL Certificate is Important for Client Trust and Google Rankings | Effortlessly Professional Websites