Creative teams now juggle massive video files, high-resolution artwork, and sensitive client data every day. Here is something most people miss. Ninety percent of creative professionals report handling confidential or proprietary files at least once a week. It sounds like standard digital hustle, right? Actually, every shared file can put your reputation and your clients at risk if you are not careful with security. There is a smarter way to protect your assets and speed up collaboration, all with the right transfer strategy.
Table of Contents
- Why Secure File Transfer Matters For Creatives
- Top Secure File Transfer Methods Explained
- Choosing The Right File Transfer Tool For Your Workflow
- Best Practices For Safe And Fast File Sharing
Quick Summary
| Takeaway | Explanation |
|---|---|
| Secure file transfer protects valuable assets | Creative professionals handle sensitive materials, making secure file transfer essential to protect against data breaches and intellectual property theft. |
| Strategic advantages include enhanced collaboration | Secure transfers facilitate improved collaboration, workflow management, and compliance, which can provide a competitive edge. |
| Encrypted cloud solutions ensure control | Utilizing encrypted cloud-based methods allows teams to manage who accesses files and maintains control over sensitive project materials. |
| Assess security and compatibility when choosing tools | Evaluate file transfer solutions based on encryption strength and protocol support to ensure they meet specific creative workflow needs. |
| Adopt best practices for safety | Implement strong encryption, user authentication, and continuous monitoring to create a secure and efficient file transfer environment. |
Why Secure File Transfer Matters for Creatives
Creative professionals handle more than just images and designs. They manage valuable intellectual property, client confidential information, and high-stakes visual assets that represent significant financial and professional investments. The stakes of secure file transfer extend far beyond simple data movement.
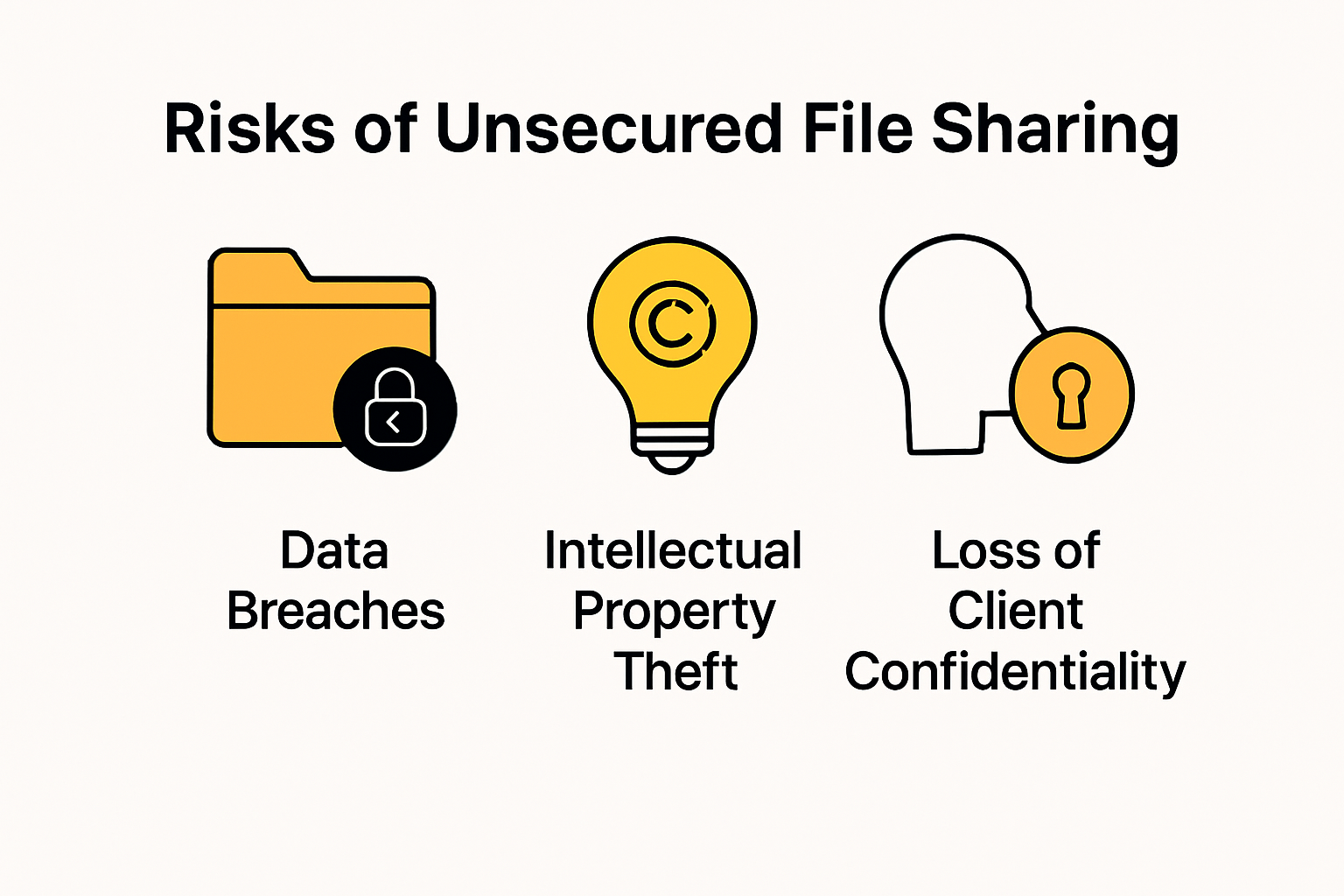
The Hidden Risks of Unsecured File Sharing
Every unprotected file transfer creates potential vulnerabilities for creative teams. Research from ResearchGate highlights that unauthorized data access can compromise entire project workflows. Photographers, videographers, and designers frequently work with files containing sensitive client information, contractual details, and proprietary visual content.
Unprotected file transfers expose professionals to multiple risks:
- Data Breaches: Unauthorized access to high-resolution images or design mockups
- Intellectual Property Theft: Potential stealing of unique creative concepts
- Client Confidentiality Violations: Accidental exposure of private project details
Compliance and Professional Reputation
Global research demonstrates that implementing robust secure file transfer methods directly impacts a creative professional’s credibility. Organizations operating in visual media must navigate complex regulatory environments. Professional teams need solutions that not only protect data but also demonstrate commitment to client trust.
Secure file transfer goes beyond technical protection. It represents a professional standard that communicates reliability, expertise, and systematic approach to client work. When creative professionals use encrypted, controlled file-sharing methods, they signal their understanding of modern digital workflow requirements.
Strategic Advantages of Secure Transfer
ShareVault’s analysis reveals that secure file transfer solutions offer strategic advantages beyond basic protection. Creative teams gain enhanced collaboration capabilities, streamlined workflow management, and comprehensive audit trails.
Key strategic benefits include:
- Granular Access Controls: Precise management of who sees specific project files
- Comprehensive Tracking: Detailed logs of file interactions and downloads
- Professional Compliance: Meeting industry standards for data protection
In an era where digital assets represent significant value, secure file transfer is not a luxury but a fundamental requirement for creative professionals. The right approach transforms file sharing from a potential risk into a strategic competitive advantage.
Top Secure File Transfer Methods Explained

Secure file transfer methods have evolved dramatically, offering creative professionals sophisticated solutions that protect digital assets while enabling seamless collaboration. Understanding these methods is crucial for maintaining data integrity and preventing unauthorized access.
Below is a summary table comparing the key secure file transfer methods mentioned in this section and their main features to help you quickly evaluate their strengths.
| Method | Main Technologies | Key Features |
|---|---|---|
| Encrypted Cloud-Based Solutions | Encrypted Container Files, Hybrid Encryption | End-to-end encryption, permission controls, metadata sanitization |
| Blockchain & Distributed Technologies | Blockchain, IPFS | Decentralized storage, immutable logs, advanced access control |
| Quantum-Resistant Transfer Methods | Post-Quantum Cryptography (CRYSTALS-Kyber, Dilithium) | Future-proof encryption, multi-layer authentication, dynamic key management |
Encrypted Cloud-Based Solutions
Advanced research from 2024 introduces Encrypted Container Files (ECF), a groundbreaking approach to secure file sharing. These hybrid-encrypted structures allow multi-recipient access while ensuring that only authorized individuals can decrypt shared files. Creative teams can leverage these technologies to maintain strict control over sensitive project materials.
Key characteristics of modern encrypted cloud solutions include:
- End-to-End Encryption: Protecting files from initial upload to final download
- Granular Permission Controls: Precise management of file access rights
- Automatic Metadata Sanitization: Removing potentially revealing file information
Blockchain and Distributed File Transfer Technologies
Innovative research demonstrates how blockchain technologies are revolutionizing secure file transfer. By integrating InterPlanetary File System (IPFS) with blockchain protocols, creative professionals can now implement advanced access control mechanisms that provide unprecedented security.
The distributed approach offers several significant advantages:
- Decentralized Storage: Eliminating single points of failure
- Immutable Transfer Logs: Creating comprehensive audit trails
Quantum-Resistant Transfer Methods
Cutting-edge research from 2025 introduces quantum-resistant file transfer systems that go beyond traditional encryption methods. These advanced solutions utilize NIST-standardized algorithms like CRYSTALS-Kyber for encryption and CRYSTALS-Dilithium for digital signatures, providing protection against emerging computational threats.
Advanced secure transfer methods now incorporate:
- Post-Quantum Cryptography: Protecting against future computational risks
- Multi-Layer Authentication: Verifying user identity through multiple mechanisms
- Dynamic Encryption Key Management: Continuously rotating encryption protocols
Creative professionals must recognize that secure file transfer is no longer a static technology. It represents a dynamic, evolving ecosystem of protection strategies designed to safeguard intellectual property in an increasingly complex digital environment. The right approach combines technological sophistication with user-friendly interfaces that make advanced security accessible and practical.
Choosing the Right File Transfer Tool for Your Workflow
Selecting the appropriate file transfer tool requires a strategic approach that considers your creative team’s unique workflow, security requirements, and collaboration needs. Not all file transfer solutions are created equal, and the wrong choice can compromise project efficiency and data protection.
To help you evaluate secure file transfer tools, this checklist summarizes key requirements and considerations that creative professionals should assess when choosing the right solution for their workflow.
| Requirement/Feature | Critical for Security | Critical for Workflow |
|---|---|---|
| End-to-End Encryption | Yes | |
| Granular Access Control | Yes | |
| Audit Trails | Yes | |
| Protocol Support (SFTP/FTPS) | Yes | |
| Cross-Platform Compatibility | Yes | |
| Workflow Integration | Yes | |
| Compliance Management | Yes | Yes |
Assessing Security and Encryption Requirements
Research from ResearchGate emphasizes the critical importance of end-to-end encryption for protecting sensitive creative assets. Creative professionals must evaluate file transfer tools based on their encryption capabilities, focusing on features that provide comprehensive protection throughout the entire file transfer process.
Key security considerations include:
- Encryption Strength: Verifying the tool’s encryption protocols
- Access Control: Implementing granular permissions for file sharing
- Audit Trails: Tracking file access and transfer history
Protocol and Compatibility Evaluation
Comprehensive research highlights the significance of secure transfer protocols like SFTP and FTPS. Creative teams should prioritize tools that support multiple transfer protocols, ensuring compatibility with various client systems and project requirements.
Important compatibility factors to consider:
- Protocol Support: SFTP, FTPS, and other secure transfer methods
- Cross-Platform Functionality: Seamless operation across different operating systems
- Integration Capabilities: Smooth connection with existing creative workflows
Managed File Transfer Solutions
Wikipedia’s analysis of Managed File Transfer reveals the advantages of comprehensive file transfer solutions for professional teams. Managed File Transfer (MFT) tools offer a more robust approach to secure file sharing, providing advanced features beyond traditional transfer methods.
Advantages of managed file transfer solutions include:
- Compliance Management: Automatic adherence to industry regulations
- Advanced Security Controls: Comprehensive protection beyond basic encryption
- Workflow Automation: Streamlining file transfer processes
Creative professionals must approach file transfer tool selection as a strategic decision. The right solution should not only protect your digital assets but also enhance collaboration, streamline workflows, and provide peace of mind. Consider your specific project requirements, team size, and the types of files you frequently transfer when making your selection.
Remember that the most expensive or feature-rich solution is not always the best fit. Prioritize tools that balance security, usability, and compatibility with your unique creative workflow. A carefully chosen file transfer tool becomes an invisible yet critical component of your professional infrastructure.
Best Practices for Safe and Fast File Sharing
Creative professionals operate in a high-stakes environment where file sharing must balance speed, security, and reliability. Implementing strategic approaches to file transfer can dramatically reduce risks while maintaining workflow efficiency.
Encryption and Access Control Strategies
Advanced security research emphasizes the critical importance of comprehensive encryption protocols. AES-256 encryption represents the gold standard for protecting files both during transfer and while stored, creating an impenetrable shield for sensitive creative assets.
Key encryption best practices include:
- Full-Cycle Encryption: Protecting files from upload to download
- Dynamic Key Management: Regularly rotating encryption keys
- Secure Transmission Channels: Using protocols that prevent interception
Authentication and User Management
Research from enterprise security experts highlights the significance of robust authentication mechanisms. Multi-factor authentication and role-based access controls transform file sharing from a potential vulnerability into a controlled, manageable process.
Effective authentication strategies involve:
- Multi-Factor Authentication: Requiring multiple verification steps
- Granular Permission Structures: Defining precise access levels
- Comprehensive User Tracking: Monitoring file interactions
Continuous Monitoring and Audit Practices
Cybersecurity analysis reveals that proactive monitoring is essential for maintaining file transfer security. Creative teams must implement systematic approaches to detect and respond to potential security incidents rapidly.
Critical monitoring components include:
- Real-Time Threat Detection: Identifying suspicious file transfer activities
- Comprehensive Logging: Maintaining detailed transfer records
- Automated Incident Response: Implementing immediate protective measures
Creative professionals must view file sharing as a strategic process requiring constant vigilance. The most effective approach combines technological solutions with human awareness. Regular training, staying updated on emerging security technologies, and developing a culture of security consciousness are equally important as implementing technical safeguards.
Remember that file sharing is not just about moving data from one point to another. It is about protecting intellectual property, maintaining client confidentiality, and preserving the professional reputation built through years of creative work. The right practices transform file transfer from a potential risk into a competitive advantage.
Frequently Asked Questions
What are the best secure file transfer methods for creative teams?
Creative teams can utilize encrypted cloud-based solutions, blockchain technologies, and quantum-resistant transfer methods to securely share files and protect sensitive data.
Why is secure file transfer important for creative professionals?
Secure file transfer is crucial for creative professionals as it protects valuable intellectual property, maintains client confidentiality, and ensures compliance with industry regulations.
How do I choose the right file transfer tool for my workflow?
When selecting a file transfer tool, consider factors such as encryption strength, protocol compatibility, access controls, and how well it integrates with your existing workflow.
What are some best practices for safe and fast file sharing?
Best practices include using strong encryption methods, implementing multi-factor authentication, conducting regular monitoring for suspicious activities, and keeping a comprehensive audit trail.
Take Creative File Sharing From Risk to Reward
Are you struggling with the stress and uncertainty of sending sensitive visuals or client files through generic transfer tools? As the article revealed, creative pros often face the real dangers of data breaches, lost control over client feedback, and clunky, unbranded galleries that make even your best work look ordinary. Secure file transfer is not just about technology. It is about protecting your reputation and building trust with every project.

Let your creative process stand out while keeping your files locked down. Pikd gives creative teams the power to upload, share, and review high-res files in beautifully branded galleries. You get encrypted file management, real-time comments, low-res previews for security, and robust permission controls. This is how you deliver peace of mind and a visual-first experience that clients will remember. See how Pikd can upgrade your workflow today at our modern platform for creative teams or explore how secure branded galleries keep your assets safe, organized, and always under your control. Join the community of photographers and visual teams who have left generic file transfer solutions behind. Try Pikd now and make every file delivery both simple and secure.